I ran into System Security a few days ago. This is one of many
rogue anti-spyware programs that pops up a now and then. I've captures some screenshots to show how users are tricked into installing this application:
While browsing some web pages the following dialog from Internet Explorer popped up. It falsely claimed that my system needed a "anti viruses check". The system is 100% clean.

If you click OK, the following will appear:

The the observant user will notice the above is just a web page that, tries to mimic the user interface of Windows XP. Web pages cannot access the local disk to scan for malware files.
If you click OK, you will get another faked scan result:
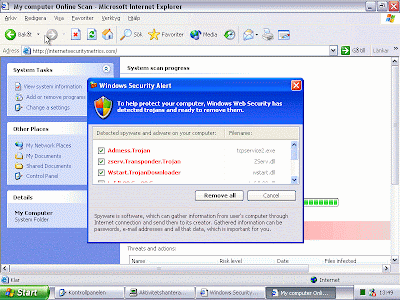
If you click "Remove all", you will get the actual installation file (install.exe):

Now it get dangerous. So far, System Security has not been able to access the system. All scan results and warnings are just faked. But if you choose to install the file install.exe you are in trouble. System security will get access to your computer:

Now that System Security got access to the system it will start showing scan results and warnings, all for the purpose of getting you to buy the program:

Here it falsely claims that some keylogger named Lsas.Blaster.Keylogger is sending my credit card information to a remote server: