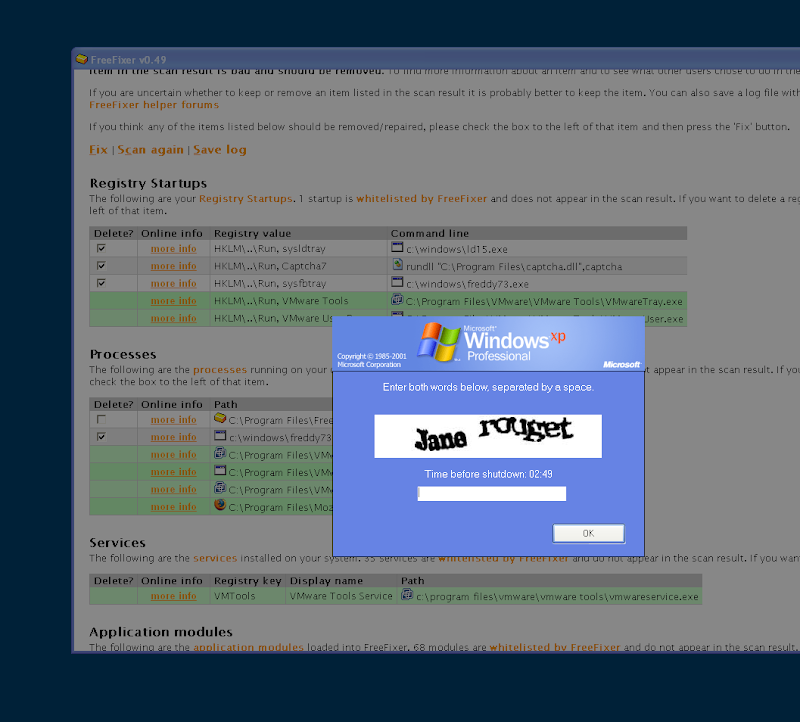
FreeFixer log below. I've highlighted the bad items in red. Hope this helps you with the removal.
FreeFixer v0.50 log
http://www.freefixer.com/
Operating system: Windows XP Service Pack 2
Log dated 2009-12-10 02:49
Registry Startups (3 whitelisted)
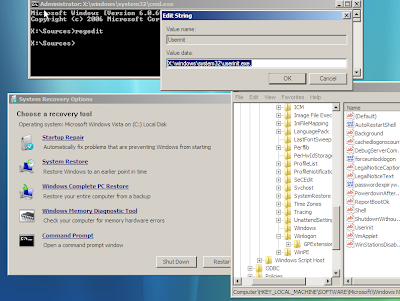
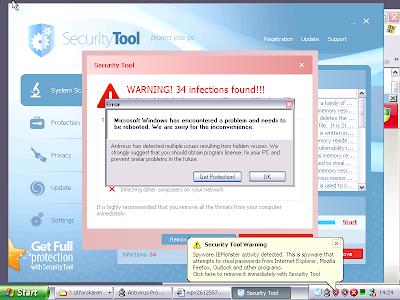
HKCU\..\Run, Internet Security 2010 = C:\Program Files\InternetSecurity2010\IS2010.exe
Processes (19 whitelisted)
C:\Program Files\FreeFixer\freefixer.exe
C:\Program Files\InternetSecurity2010\IS2010.exe
Recently created/modified files
0 minutes, c:\Program Files\InternetSecurity2010\IS2010.exe
0 minutes, c:\Documents and Settings\roger\Local Settings\Temporary Internet Files\Content.IE5\O1EF052R\SetupIS2010[1].exe