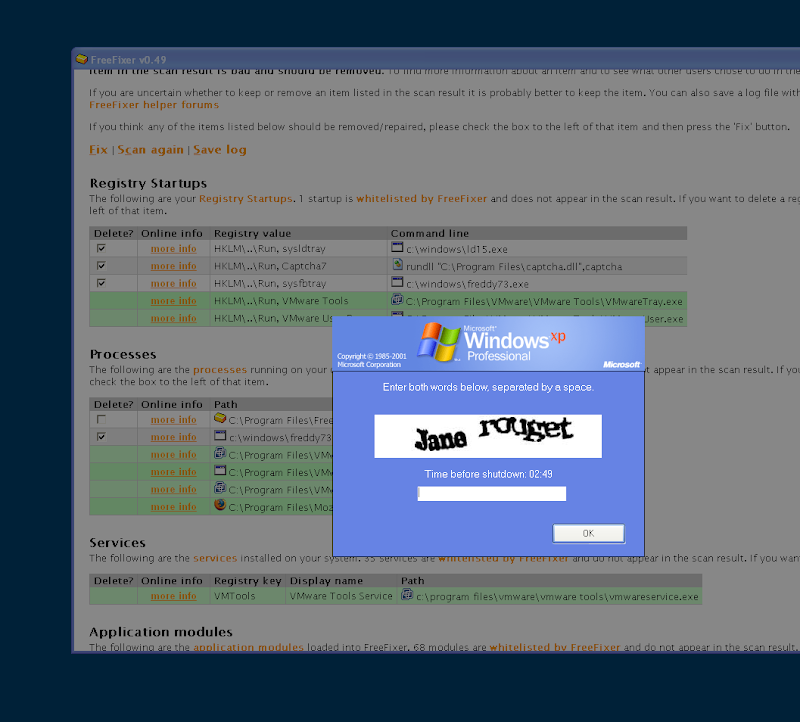
I've pasted the FreeFixer log from the infected system. Everything is malware except freefixer.exe:
FreeFixer v0.49 log
http://www.freefixer.com/
Operating system: Windows XP Service Pack 2
Log dated 2009-11-14 01:55
Registry Startups (3 whitelisted)
HKLM\..\Run, sysldtray = c:\windows\ld15.exe
HKLM\..\Run, Captcha7 = rundll "C:\Program Files\captcha.dll",captcha
HKLM\..\Run, sysfbtray = c:\windows\freddy73.exe
Processes (19 whitelisted)
C:\Program Files\FreeFixer\freefixer.exe
c:\windows\freddy73.exe
Recently created/modified files
8 minutes, c:\Documents and Settings\roger\Local Settings\Temporary Internet Files\Content.IE5\WEGR55JE\v2googlecheck[1].exe
8 minutes, c:\Program Files\captcha.dll
8 minutes, c:\Documents and Settings\roger\Local Settings\Temporary Internet Files\Content.IE5\6CSRVCZ7\v2captcha[1].exe
20 minutes, c:\WINDOWS\zwer_1258158897.exe
20 minutes, c:\Documents and Settings\roger\Local Settings\Temporary Internet Files\Content.IE5\6CSRVCZ7\v2googlecheck[1].exe
20 minutes, c:\Documents and Settings\roger\Local Settings\Temporary Internet Files\Content.IE5\4HUF4TYN\v2captcha[1].exe
20 minutes, c:\WINDOWS\freddy73.exe
20 minutes, c:\Documents and Settings\roger\Local Settings\Temporary Internet Files\Content.IE5\O1EF052R\fb[1].73.exe
20 minutes, c:\Documents and Settings\roger\Local Settings\Temporary Internet Files\Content.IE5\6CSRVCZ7\get[1].exe
21 minutes, c:\Documents and Settings\roger\Local Settings\Temporary Internet Files\Content.IE5\4HUF4TYN\ff2ie[1].exe
21 minutes, c:\WINDOWS\ld15.exe
End of FreeFixer log